What's Operation Global III?
Operation Global III is a group of a botnet/malware, ransomware, and a screen locker. It is such a malicious program that not only encrypts victim users' files (including all images, pdf files, rar files and setups...) blocking their access to the files, but also places a lock on their screens, preventing them from fixing the issue. By requiring the victims to pay money for the key or code to file decryption, Operation Global III can help its designers make money.
Operation Global III pops up a message on your screen, telling that All your important files are encrypted and you need to pay a $250 fine to get your files decryted. It warns that changing the name of any encrypted file will cause the file locked forever. It leaves a note telling you where and how to pay the fine.

How Does Operation Global III Ransom Virus Get on Your Computer?
Operation Global III ransomware can be hidden with malicious links in spam attachments, e-mail messages, instant messages, social networking sites. When you click those malicious links, you may have the ransomware installed on your computer. usually installed extortion software on your computer. This blackmail / extortion software can even be installed when you visit a hacked/compromised site.
What Will Operation Global III Ransomware Do?
- Once executed on the computer, Operation Global III starts encrypting files that are thought important for the user.
- Operation Global 3 modifies relevant settings and flashes a blackmail message on the screen when the operation completes.
- This ransomware is deemed to be developed in .NET and has keylogging functionality.
- It can terminate the activity of certain tools such as Task Manager, CMD, Regedit, msconfig, PowerShell, Windows Backup or System Restore etc.
Are You Going to Pay for Operation Global III?
You may wonder whether it is time to say goodbye to all of the infected files or anyone has any idea what to do to decrypt them. Never be taken in! Actually, computer experts haven't found a good way with efficiency to fix this issue. Cracking file highly encrypt Operation Global III is almost impossible. If you do not pay the ransom, you may lose everything. Lots of ransomware programs have been proven scam. We can't promise that you will get your files back by paying for the criminals.
Any Possible Ways to Restore You Files Encrypted by Operation Global III?
Option One: Restore your files from a recent backup. If you are performing backups regularly, then you could restore your files using your backups.
Option Two: Restore previous versions of files via using Windows folder tools. (Right-click the file or folder, and then click Restore previous versions.)
You can have more information here: About Previous versions of files.
Option Three (the infection active only) : It is said that the OG3 Patcher from BleepingComputer might be helpful. According concerned party, users just need to download the tool from http://download.bleepingcomputer.com/Nathan/og3patcher.exe. And then click the downloaded file and click “Patch” to have their files decrypted.
How to Remove Operation Global III Ransom Virus Manually?
Video Guide for Ransom Virus Removal (Reference)
How to Remove Operation Global III Automatically with Removal Tool SpyHunter?
1) Download and install ransom virus remover SpyHunter
a) Click the icon below to download the removal tool automatically
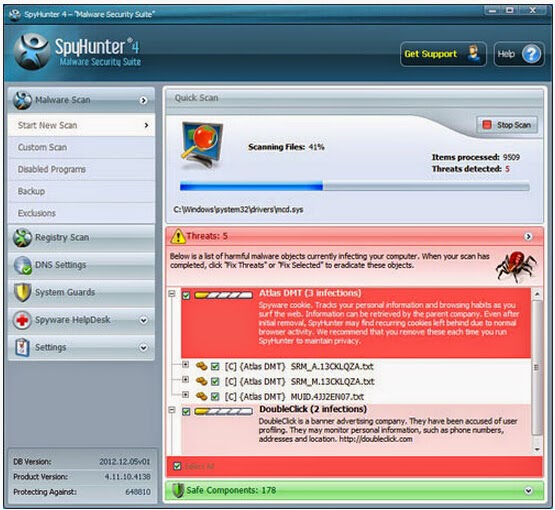
2) Run SpyHunter to scan your computer for this ransom invader
Click "Start New Scan" button to scan your computer
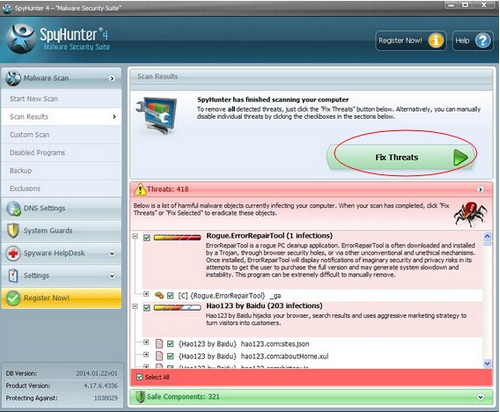
3) Get rid of all detected items by clicking "Fix Threats" button
What to Learn from Operation Global III Invasion?
There are so many ransomware programs performing malicious actions and you may have heard some such as: HowDecrypt, DirtyDecrypt, Crytolocker, Cryptowall, TeslaCrypt, Fud@india.com, Decode@india.com, CoinVault, Critroni, PowerLocker ransom trojan and so on. Ransomware programs can make their ways to users’ systems via every opening. To avoid further damage, you are suggested to be highly attention.
* Avoid opening unknown sources, especially in ZIP or RAR file format for e-mail attachments.
* Update your operating system and your anti-virus software. Scan the machine regularly.
* If you have a real-time backup software, so please clean up your computer and then restored.
* Create a network disk in the cloud, the documents and photographs to back up to the top.
* If you are a Windos 7 user, you could set a system restore point.
A Word of Advice:
Anything committing blackmail like Operation Global III should be eliminated quickly. If the manual solution is kind of complicated for you, please feel free to start an automatic removal with the most popular antivirus program - SpyHunter. This antivirus will not only help erasing infection at this moment, but also provide powerful, real-time protection in the future.

No comments:
Post a Comment