Browse Table of contents
- What is Crypto Wall 3.0?
- What will Crypto Wall 3.0 do after logging in your PC?
- What kind of files can be encrypted by Crypto Wall 3.0?
- What should you do after being infected with Crypto Wall 3.0?
- What could you do to prevent Crypto Wall 3.0?
- About the encrypted files, what can you do now?
- Will you get back your files after paying the ransom?
- What you really really need to know.
What is Crypto Wall 3.0 ( Crypto Wall 2.0)?
Crypto Wall 3.0 ( Crypto Wall 2.0)is one kind of ransomware which is created to blackmail money by encrypting files. It is released lately and spread crazily around the Internet. All versions of Windows including Windows XP, Windows 7, Windows Vista and Windows 8 are its targets as well as Mac OS. After the encryption, Crypto Wall 3.0 will display a window containing the ransom message and instructions on how to get back your files. There is a link among the instructions, informing the current ransom amount and the amounts of the encrypted files. Of course it won’t forget to tell you how to make your payment. The ransom cost begin with $300 and it will go up after 3 days, which obviously a huge threats.

He haven't noticed that Crypto Wall 3.0 is scanning his files to encrypt.
"I knew this was going to be hard to do!! A strange screen called 'Crypto Wall 3.0' has appeared when I click on IE. I am unable to clip and snip and all that other stuff to show anyone. All I need to know is what do I click on to put it in the recycle bin???"
What will Crypto Wall 3.0 do after logging in your PC?
As soon as it logs in your PC, it begins to scan your PC for data files and encrypt them by AES encryption, which leads to a result that they are no longer able to be opened. It definitely encrypts it when Crypto Wall 3.0 detects a supported data file and them append ‘.encrypted’ to the file name.

What kind of files can be encrypted by Crypto Wall 3.0?
What needs to stress: Crypto Wall 3.0 2will scan all drive letter on your PC including removable drives, network shares.
The files that can be encrypted contain the following file extensions:
*.xlsb, *.xltm, *.xltx, *.xlsm, *.xlsx, *.xlm, *.xlt, *.xls, *.xml, *.ppsm, *.ppsx, *.ppam, *.potm, *.potx, *.pptm, *.pptx, *.pps, *.pot, *.ppt, *.xlw, *.xll, *.xlam, *.xla, *.dotm, *.dotx, *.docm, *.docx, *.dot, *.doc, *.txt, *.wb2, *.psd, *.p7c, *.p7b, *.p12, *.pfx, *.pem, *.crt, *.cer, *.der, *.pl, *.py, *.lua, *.css, *.js, *.asp, *.php, *.incpas, *.asm, *.hpp, *.h, *.cpp, *.c, *.7z, *.zip, *.rar, *.drf, *.blend, *.apj, *.3ds, *.dwg, *.sda, *.ps, *.pat, *.fxg, *.fhd, *.fh, *.dxb, *.drw, *.design, *.ddrw, *.ddoc, *.dcs, *.csl, *.csh, *.cpi, *.cgm, *.cdx, *.cdrw, *.cdr6, *.cdr5, *.cdr4, *.cdr3, *.cdr, *.awg, *.ait, *.ai, *.agd1, *.ycbcra, *.x3f, *.stx, *.st8, *.st7, *.st6, *.st5, *.st4, *.srw, *.srf, *.sr2, *.sd1, *.sd0, *.rwz, *.rwl, *.rw2, *.raw, *.raf, *.ra2, *.ptx, *.pef, *.pcd, *.orf, *.nwb, *.nrw, *.nop, *.nef, *.ndd, *.mrw, *.mos, *.mfw, *.mef, *.mdc, *.kdc, *.kc2, *.iiq, *.gry, *.grey, *.gray, *.fpx, *.fff, *.exf, *.erf, *.dng, *.dcr, *.dc2, *.crw, *.craw, *.cr2, *.cmt, *.cib, *.ce2, *.ce1, *.arw, *.3pr, *.3fr, *.mpg, *.jpeg, *.jpg, *.mdb, *.sqlitedb, *.sqlite3, *.sqlite, *.sql, *.sdf, *.sav, *.sas7bdat, *.s3db, *.rdb, *.psafe3, *.nyf, *.nx2, *.nx1, *.nsh, *.nsg, *.nsf, *.nsd, *.ns4, *.ns3, *.ns2, *.myd, *.kpdx, *.kdbx, *.idx, *.ibz, *.ibd, *.fdb, *.erbsql, *.db3, *.dbf, *.db-journal, *.db, *.cls, *.bdb, *.al, *.adb, *.backupdb, *.bik, *.backup, *.bak, *.bkp, *.moneywell, *.mmw, *.ibank, *.hbk, *.ffd, *.dgc, *.ddd, *.dac, *.cfp, *.cdf, *.bpw, *.bgt, *.acr, *.ac2, *.ab4, *.djvu, *.pdf, *.sxm, *.odf, *.std, *.sxd, *.otg, *.sti, *.sxi, *.otp, *.odg, *.odp, *.stc, *.sxc, *.ots, *.ods, *.sxg, *.stw, *.sxw, *.odm, *.oth, *.ott, *.odt, *.odb, *.csv, *.rtf, *.accdr, *.accdt, *.accde, *.accdb, *.sldm, *.sldx.
After the encryption, it will create a ransom note located at %UserProfile%\Desktop. The file name and the ransom note will changed according your IP address.
What should you do after being infected with Crypto Wall 3.0?
Here is the unfortunate thing. Most of the people don’t know that Crypto Wall 3.0 is on their PC until the ransom note appears and all the files have been encrypted. Don’t underestimate the scan. It not only can detect and remove Crypto Wall 3.0 but also help you get rid of other malware that may have been installed along with Crypto Wall 3.0.
Now Download and Install the antivirus program to block Crypto Wall 3.0 and other sorts of bugs.
Remove Crypto Wall 3.0 with the Automatic Removal Tool

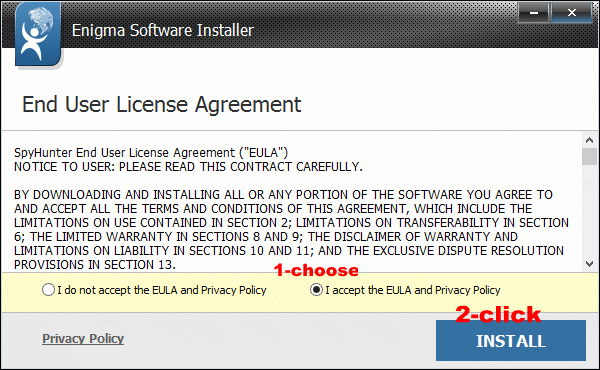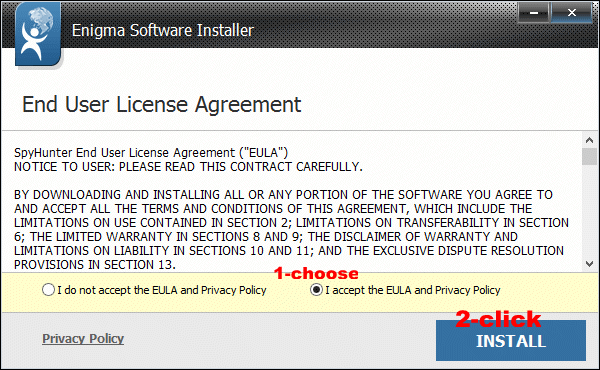
(You have 2 options for you: click Save or Run to install the program. You are suggested to save it on the desktop if you choose Save so that you can immediately start the free scan by clicking the desktop icon.)
2. The pop-up window box below needs your permission for the setup wizard. Please click Run.
Continue to follow the setup wizard to install the Automatic Removal Tool.
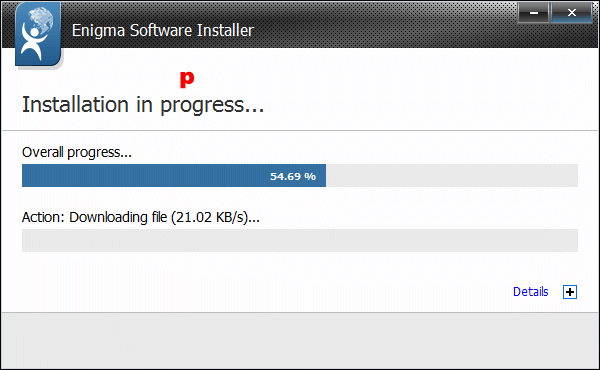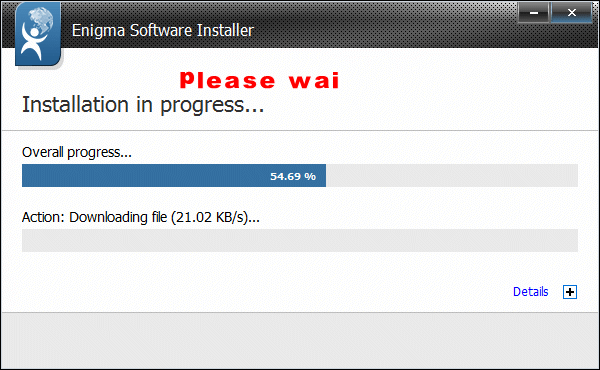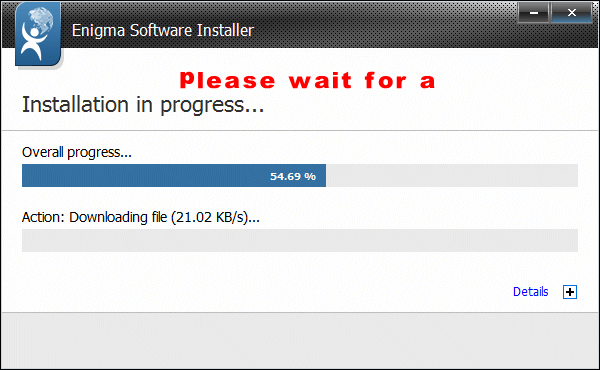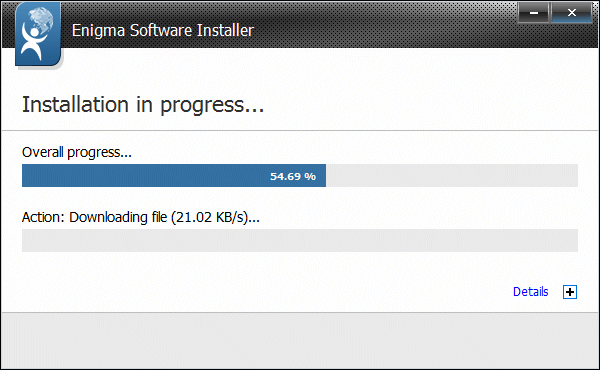
It may take a while to download all the files. Please be patient.
No More Hesitation. Time to scan your PC. Please click Start New Scan/ Scan Computer Now!
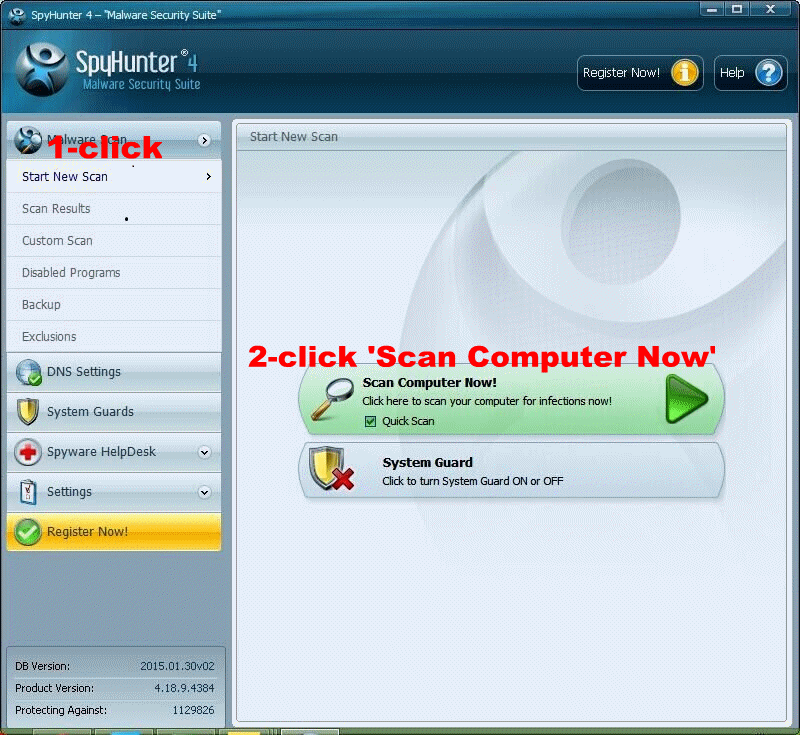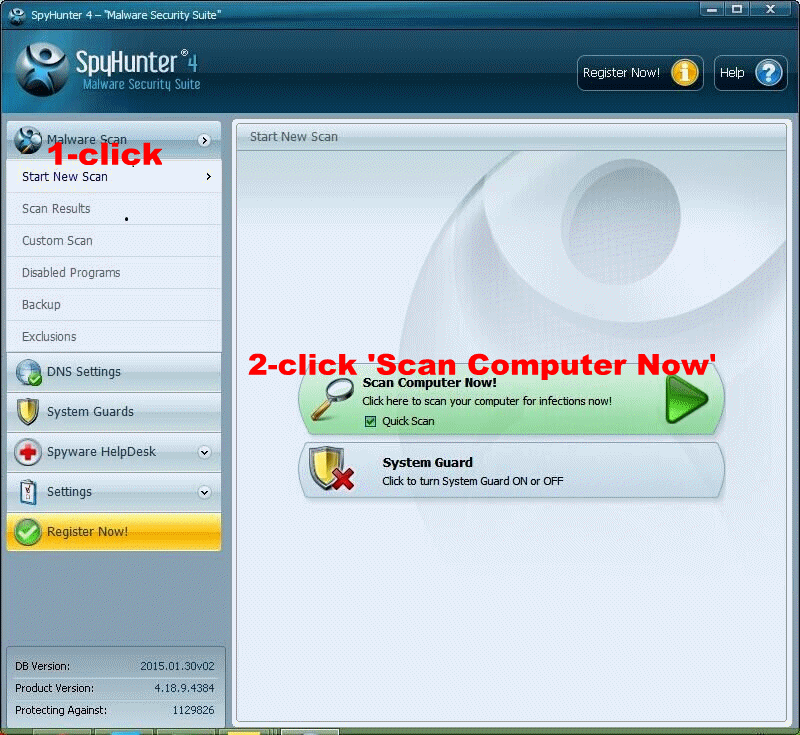
Scanning your PC now <<<<<<<<
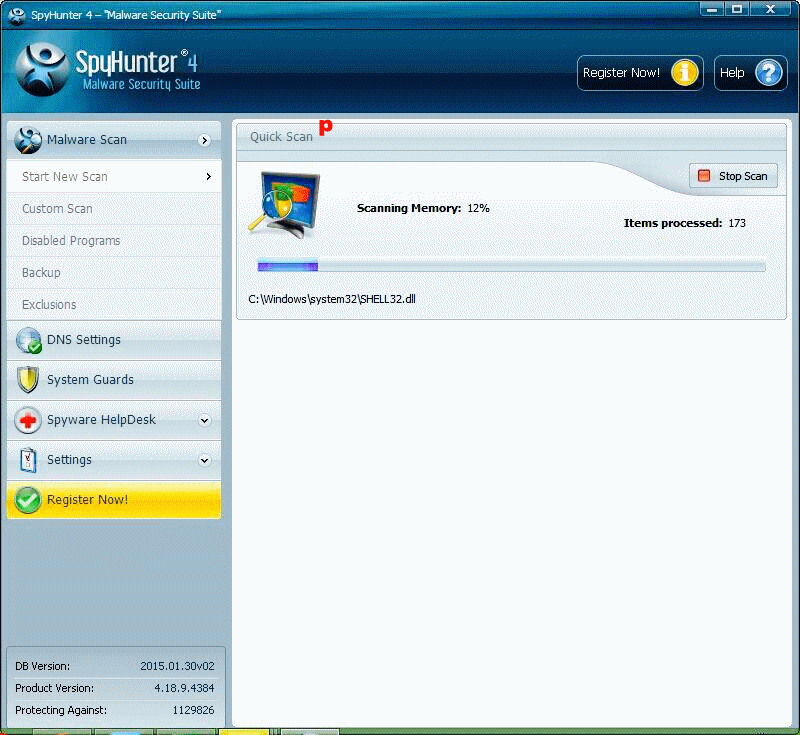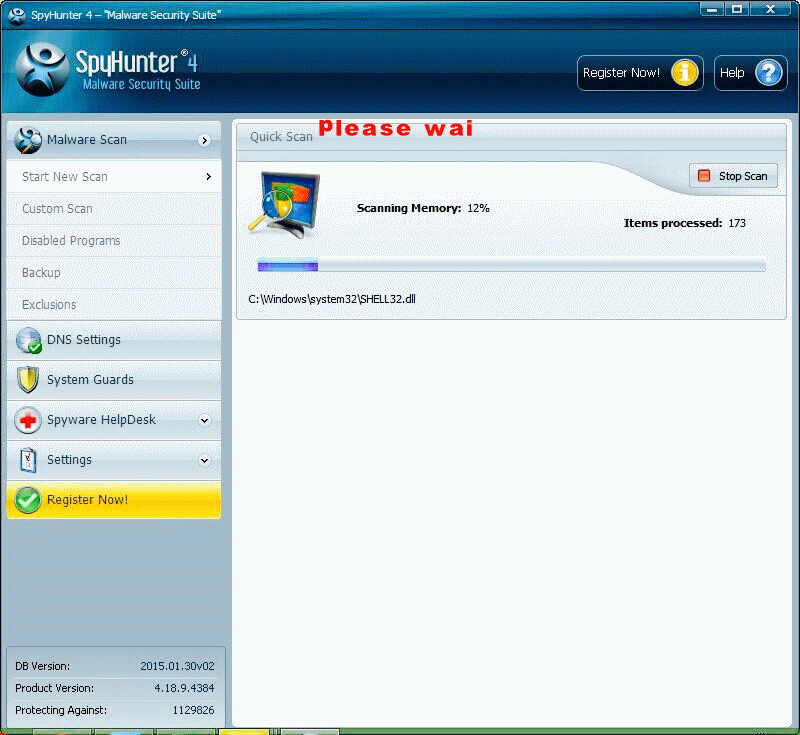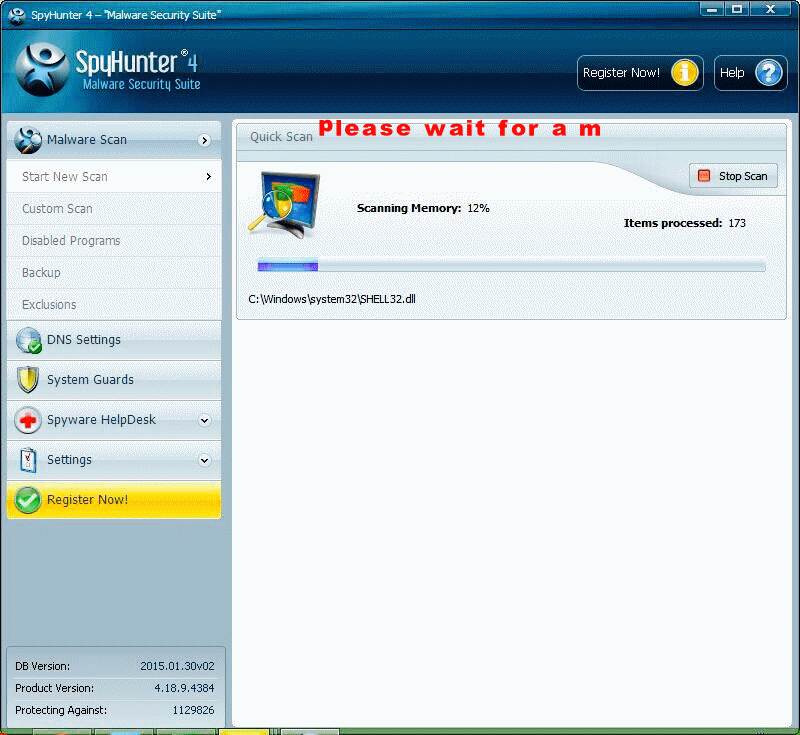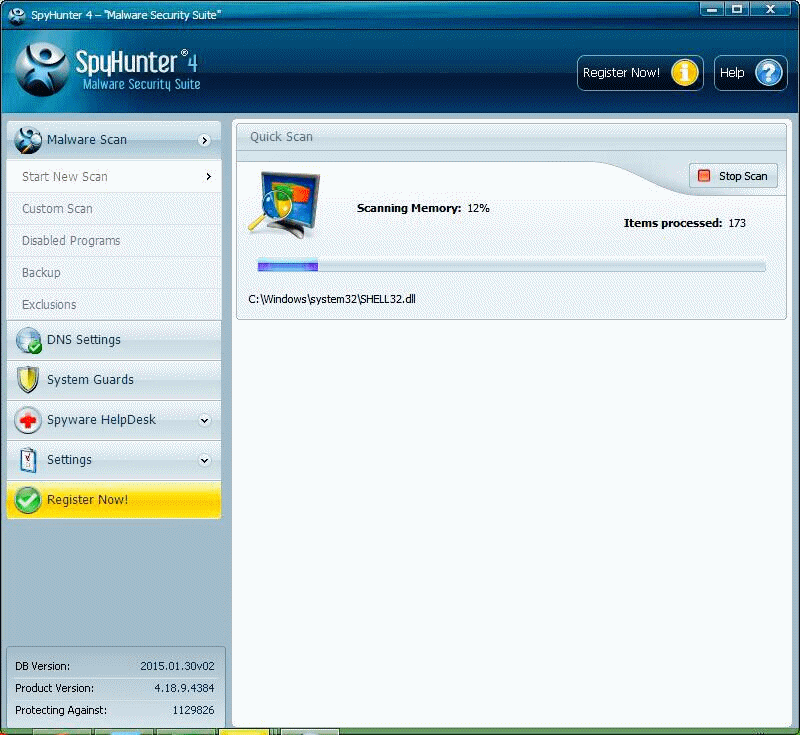
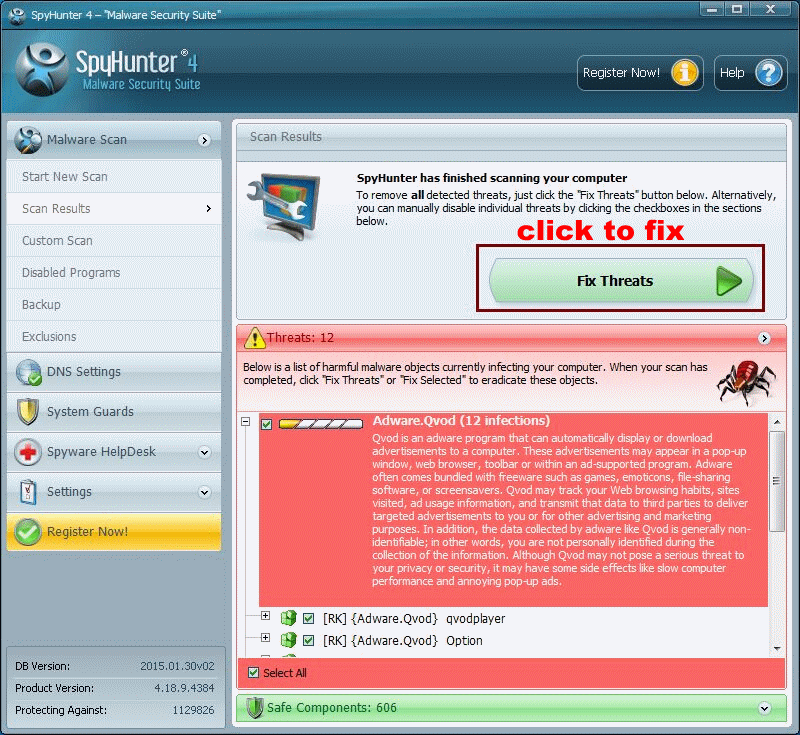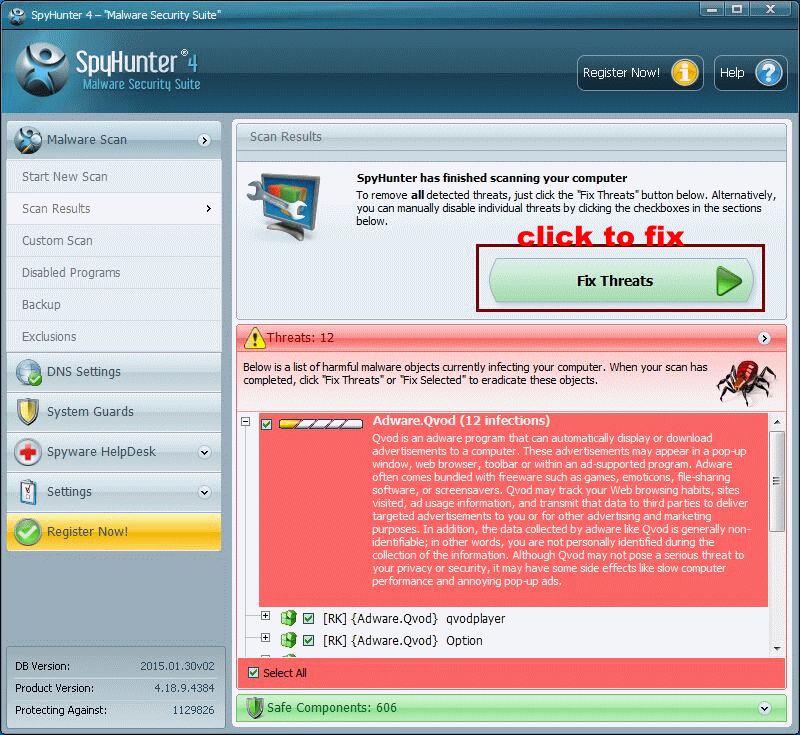
This is what you should do for so many reasons: click Fix Threats.
You are strongly suggested:
If your PC is hit by Crypto Wall 3.0, you shouldn't ignore the scan results which are real and you need to take action immediately. If you are a computer savvy, download the strong and powerful virus-removal software to terminate Crypto Wall 3.0.
What could you do to prevent Crypto Wall 3.0?
1. Do not open strange email attachments.
2. Do not click unfamiliar or malicious links.
3. Do not browse the corrupted or unreliable websites especially porno related.
About the encrypted files, what can you do now?
Path 1: backups
As a computer user and since the computer is your working tool, you should develop a good habbit: backup. You can use your backups to restore your files if you have performed the backups. Learn the lesson from Crypto Wall 3.0 – do backups
Path 2: use file-recovery software
You stand a chance to restore your files via using file recovery software. The encrypted files you see is the copy that Crypto Wall 3.0 makes. It makes a copy and then encrypted them. The original ones have been deleted. Due to this, you are able to use the file recovery software to recover some of your original files.
Path 3: Shadow Copies.
You can try to get back part of your files via Shadow Copies. If you are lucky enough that Crypto Wall 3.0 fails to delete any Shadow Copies, you can use it to restore your files. (note: the files you can get back from Shadow Copies is up to 64.)
Will you get back your files after paying the ransom?
It’s not a sure thing than you can get back your files after paying the ransom. But the sure thing is that your paying encourages the ransomware creator to collect money by encrypting more and more files by spreading ransomware like Crypto Wall 3.0.
What you really really need to know:
Crypto Wall 3.0, like other malware, it would never ever come alone. It will definitely invites friends like adware, browser hijacker and trojan. What you really should do now is to ask help from an powerful antivirus program to help you clear the malware out. Click to download and install SpyHunter now.
( Kris)

No comments:
Post a Comment